Which Osi Layer Provides File Transfer Services
Both TCP and UDP provide a port identifier to uniquely identify each data stream. A set of standard port numbers are assigned by the IANA to the major aplication layer protocols. These 'well known' ports make it easier to find the corresponding server for a particular protocol on a host. Application Layer. The Application layer is the OSI layer closest to the end user, which means that both the OSI Application layer and the user interact directly with the software application. Application layer functions typically include file transfer, file management, message handling, and database query functions. Layer 7 – Application. The Application layer is the main layer of the OSI model, and it provides the interface between the network protocol and the software running on the computer. The Application layer provides the necessary services that support applications. It provides the interface for e-mail, Telnet and File Transfer Protocol (FTP).
- Which Osi Layer Provides File Transfer Services Near Me
- Osi Layer Protocols
- Osi Model Layer 2 Protocols
- Which Osi Layer Provides File Transfer Services Online
- Physical Layer Osi
What is OSI 7 Layer Model?
In 1978, ISO developed an architecture that would allow the devices of different manufacturers to work together to communicate with different operating systems. In 1984, the ISO architecture became an international standard known as the Open Systems Interconnection (OSI) reference model.
This architecture determines how hardware, software,topologies, and protocols exist and operate on a network. The OSI model is based on seven layers, as shown in the following figure. Each layer adds functionality to the previous layer and communicates with the layers directly above and below it.
This model defines seven Layers that describe how applications running upon network-aware devices may communicate with each other. The model is generic and applies to all network types, not just TCP/IP, and all media types, not just Ethernet.
In an exchange between users, there will be a flow of data through each layer at one end down through the layers in that computer; and when the message arrives at its destination, there will be another flow of data up through the layers in the receiving computer that ultimately ends up at the application.
The seven layers of the OSI reference model can be divided into two categories: upper layers and lower layers. The upper layers of the OSI model deal with application issues and generally are implemented only in software. The lower layers of the OSI model handle data transport issues. The physical layer and the data link layer are implemented in hardware and software.
It should be noted, however, that most protocols in day-to-day use work on a slightly modified layer system. TCP/IP, for example, uses a 6- rather than a 7-layer model. Nevertheless, in order to ease the exchange of ideas, even those who only ever use TCP/IP will refer to the 7-layer model when discussing networking principles with peers from a different networking background.
1. Physical Layer
The Physical layer (Layer 1) handles the mechanical and electrical communications. In other words, it translates bits (0s and 1s) into data that can be transmitted.
Layer 1 specifications determine the shape, size, and pin-out of connectors; what voltages and currents are used; and how the physical media and electrical components work together.
Devices that operate at the Physical layer include network interface cards (NIC), hubs, repeaters, multistation access units, media filters, and transceivers.
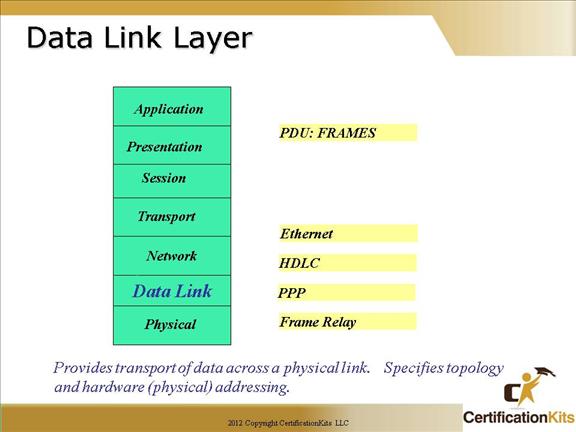
2. Data Link Layer
The Data Link layer (Layer 2) provides flow, error control, and synchronization for the Physical layer. It takes information from the Network layer and sends it to the intended device through the Physical layer on the same network.
The specifications defined at this layer are network and protocol characteristics. This includes physical addressing, network topology, error notification, sequencing of frames, and flow control.
- Physical addressing defines how devices are addressed.
- Network topology determines the specifications that define how devices are to be physically connected.
- Error notification alerts upper-layer protocols that a transmission error has occurred.
- Sequencing reorders frames that are transmitted out of order.
- Flow control monitors the transmission of data so that the receiving device is not overwhelmed with more traffic than it can handle at one time.
3. Network Layer
The Network layer (Layer 3) manages the routing of packets that are to be forwarded on to different networks.
The Network layer relies on the use of routable protocols to deliver packets to distant networks. The Network layer defines the network address, which is different from the MAC (Media Access Control) address. The MAC address is considered the physical address, and the network address is considered the logical address.
Because this layer defines the logical network layout, routers can use it to determine how to forward packets. Because routers function at this layer,much of the design and configuration of a network is done here.
See the following figure for examples of the devices that operate on the first three layers of the OSI model.
The Network Layer provides the functional and procedural means of transferring variable length data sequences from a source host on one network to a destination host on a different network, while maintaining the quality of service requested by the Transport Layer (in contrast to the data link layer which connects hosts within the same network). The Network Layer performs network routing functions, and might also perform fragmentation and reassembly, and report delivery errors. Routers operate at this layer—sending data throughout the extended network and making the Internet possible. This is a logical addressing scheme – values are chosen by the network engineer. The addressing scheme is not hierarchical.
The Network Layer may be divided into three sub-layers:
- Subnetwork Access – that considers protocols that deal with the interface to networks, such as X.25;
- Subnetwork Dependent Convergence – when it is necessary to bring the level of a transit network up to the level of networks on either side
- Subnetwork Independent Convergence – which handles transfer across multiple networks.
4. Transport Layer
The Transport layer (Layer 4) manages the connection between the source and the destination to ensure that the data has reliable delivery. The Transport layer accepts data and segments it for transport across the network. Generally, the Transport layer is responsible for making sure that the data is delivered error free and in the proper sequence.
Flow control generally occurs at the Transport layer. Flow control manages data transmission between devices so that the transmitting device does not send more data than the receiving device can process.
Reliable delivery involves error checking and recovery. Error checking involves detecting transmission errors, while error recovery involves acting to resolve any errors that occur.
Transport protocols can be characterized as being either connection-oriented or connectionless. In general, connection-oriented services provide some level of delivery guarantee, whereas connectionless services do not.
- Connection-oriented services must first establish a connection with the desired service before passing any data.
- A connectionless service can send the data without any need to establish a connection first.
Connection-oriented service involves three phases: establishing the connection, transferring the data, and terminating the connection. The protocol is also responsible for putting the packets in the correct sequence before passing on the data. Connection-oriented network services have more overhead than connectionless ones. Connection-oriented services must negotiate a connection, transfer data, and tear down the connection, whereas a connectionless transfer can simply send the data without the added overhead of creating and tearing down a connection.
An example of this is similar to the difference between regular mail and certified mail. Using regular mail delivery, you mail a letter and assume it will get there. Using certified mail delivery, the Post Office contacts the recipient, gives them the mail, and makes them sign for it.
OSI defines five classes of connection-mode transport protocols ranging from class 0 (which is also known as TP0 and provides the least features) to class 4 (TP4, designed for less reliable networks, similar to the Internet). Class 0 contains no error recovery, and was designed for use on network layers that provide error-free connections. Class 4 is closest to TCP, although TCP contains functions, such as the graceful close, which OSI assigns to the Session Layer. Also, all OSI TP connection-mode protocol classes provide expedited data and preservation of record boundaries. Detailed characteristics of TP0-4 classes are shown in the following table:
5. Session Layer
The Session layer (Layer 5) manages the communication between the applications after a connection is made. It sets up the session, manages the information exchanges, and then breaks it down when the session ends.
The Session layer establishes, manages, and terminates communication sessions. These sessions consist of service requests and responses that occur between applications located in different network devices. The sessions are coordinated by protocols implemented at this layer. It also monitors the identification of the session participants to be sure that only nodes that are authorized can participate in the session.
An example of this is a conference call. To connect, you need a participant number. The call is usually run by a moderator who decides who can talk and for how long. The call ends when the moderator disconnects.
The Session Layer controls the dialogues (connections) between computers. It establishes, manages and terminates the connections between the local and remote application. It provides for full-duplex, half-duplex, or simplex operation, and establishes checkpointing, adjournment, termination, and restart procedures. The OSI model made this layer responsible for graceful close of sessions, which is a property of the Transmission Control Protocol, and also for session checkpointing and recovery, which is not usually used in the Internet Protocol Suite. The Session Layer is commonly implemented explicitly in application environments that use remote procedure calls.
6. Presentation Layer
Which Osi Layer Provides File Transfer Services Near Me
The Presentation layer (Layer 6) formats the data for exchange between the Application layer and the Session layer. Data compression and encryption also occur at this layer. This layer converts incoming and outgoing data from one presentation format to another through the use of standard image, sound, and video formats; standard data compression schemes; and standard data encryption schemes.
Presentation layer implementations are not typically associated with a particular protocol stack. Some well-known standards include Motion Picture Experts Group (MPEG), Graphics Interchange Format (GIF), Joint Photographic Experts Group (JPEG), and Tagged Image File Format (TIFF).
This is where application data is either packed or unpacked, ready for use by the running application. Protocol conversions, encryption/decryption and graphics expansion all takes place here.
The Presentation Layer establishes context between Application Layer entities, in which the higher-layer entities may use different syntax and semantics if the presentation service provides a mapping between them. If a mapping is available, presentation service data units are encapsulated into session protocol data units, and passed down the stack.
This layer provides independence from data representation (e.g., encryption) by translating between application and network formats. The presentation layer transforms data into the form that the application accepts. This layer formats and encrypts data to be sent across a network. It is sometimes called the syntax layer.
The original presentation structure used the basic encoding rules of Abstract Syntax Notation One (ASN.1), with capabilities such as converting an EBCDIC-coded text file to an ASCII-coded file, or serialization of objects and other data structures from and to XML.
7. Application Layer
The Application layer (Layer 7) provides the user interface for communication. The Application layer is the OSI layer closest to the end user, which means that both the OSI Application layer and the user interact directly with the software application. Application layer functions typically include file transfer, file management, message handling, and database query functions.
The Application layer also determines the availability of an application with data to transmit, and decides whether sufficient network resources for the communication exist. The Application layer is not itself an application that is communicating; rather it is a layer that provides application services. Some examples of Application layer implementations include Telnet, File Transfer Protocol (FTP), and Simple Mail Transfer Protocol (SMTP).
Application layer functions typically include identifying communication partners, determining resource availability, and synchronizing communication. When identifying communication partners, the application layer determines the identity and availability of communication partners for an application with data to transmit. When determining resource availability, the application layer must decide whether sufficient network or the requested communication exist. In synchronizing communication, all communication between applications requires cooperation that is managed by the application layer.
Some examples of application layer implementations also include:
On OSI stack:
- FTAM File Transfer and Access Management Protocol
- X.400 Mail
- Common management information protocol (CMIP)
On TCP/IP stack:
- Hypertext Transfer Protocol (HTTP)
- File Transfer Protocol (FTP)
- Simple Mail Transfer Protocol (SMTP)
- Simple Network Management Protocol (SNMP)
>> OSI 7 Layer Model Examples in Different Protocols
| OSI model by layer |
|---|
|
|
In the seven-layer OSI model of computer networking, the presentation layer is layer 6 and serves as the data translator for the network.[1][2] It is sometimes called the syntax layer.[3]
- 3Sublayers
Description[edit]
The presentation layer is responsible for the formatting and delivery of information to the application layer for further processing or display.[4] It relieves the application layer of concern regarding syntactical differences in data representation within the end-user systems. An example of a presentation service would be the conversion of an EBCDIC-coded text computer file to an ASCII-coded file.
The presentation layer is the lowest layer at which application programmers consider data structure and presentation, instead of simply sending data in the form of datagrams or packets between hosts. This layer deals with issues of string representation - whether they use the Pascal method (an integer length field followed by the specified amount of bytes) or the C/C++ method (null-terminated strings, e.g. 'thisisastring0'). The idea is that the application layer should be able to point at the data to be moved, and the presentation layer will deal with the rest.
Serialization of complex data structures into flat byte-strings (using mechanisms such as TLV or XML) can be thought of as the key functionality of the presentation layer.
Encryption is typically done at this level too, although it can be done on the application, session, transport, or network layers, each having its own advantages and disadvantages.[1]Decryption is also handled at the presentation layer. For example, when logging on to bank account sites the presentation layer will decrypt the data as it is received.[1] Another example is representing structure, which is normally standardized at this level, often by using XML. As well as simple pieces of data, like strings, more complicated things are standardized in this layer. Two common examples are 'objects' in object-oriented programming, and the exact way that streaming video is transmitted.
In many widely used applications and protocols, no distinction is made between the presentation and application layers. For example, HyperText Transfer Protocol (HTTP), generally regarded as an application-layer protocol, has presentation-layer aspects such as the ability to identify character encoding for proper conversion, which is then done in the application layer.
Right hemisphere deep exploration cad edition. Oct 05, 2012 Right.Hemisphere.Deep.Exploration.CAD.Edition.v6.5.0.x64. Discussion in '3D' started by mrbigbang, Oct 5, 2012. Mrbigbang Member. Joined: May 20, 2012 Messages: 5 Likes Received: 1. Deep Exploration is a graphics manipulation tool, which helps you create and publish 2D and 3D product graphics, by using default CAD models offered,. Right Hemisphere Deep Exploration CAD Edition 6.5.0 (x86)| 563 MbDeep Exploration CAD Edition enables your extended teams to easily create and deliver visual product. Download 64 Bit Deep Exploration 6.5 - best software for Windows. Deep Exploration: Deep Exploration is a graphics manipulation tool, which helps you create.

Within the service layering semantics of the OSI network architecture, the presentation layer responds to service requests from the application layer and issues service requests to the session layer.
In the OSI model: the presentation layer ensures the information that the application layer of one system sends out is readable by the application layer of another system. For example, a PC program communicates with another computer, one using extended binary coded decimal interchange code (EBCDIC) and the other using ASCII to represent the same characters. If necessary, the presentation layer might be able to translate between multiple data formats by using a common format.
Services[edit]
- Data conversion[2]
- Character code translation[2]
- Compression[2]
- Encryption and Decryption[2]
Sublayers[edit]
The presentation layer can be composed of two sublayers: common application service element (CASE) and specific application service element (SASE).[5]
CASE[edit]
The common application service element sublayer provides services for the application layer and request services from the session layer.It provides support for common application services, such as:
Osi Layer Protocols
- ACSE (Association Control Service Element)[5]
- ROSE (Remote Operation Service Element)
- CCR (Commitment Concurrency and Recovery)
- RTSE (Reliable Transfer Service Element)
SASE[edit]
The specific application service element sublayer provides application specific services (protocols), such as
- FTAM (File Transfer, Access and Manager)
- VT (Virtual Terminal)
- MOTIS (Message Oriented Text Interchange Standard)
- CMIP (Common Management Information Protocol)
- JTM (Job Transfer and Manipulation) a former OSI standard
- MMS (Manufacturing Messaging Service)
- RDA (Remote Database Access)
- DTP (Distributed Transaction Processing)
Protocols[edit]
Other protocols sometimes considered at this level (though perhaps not strictly adhering to the OSI model) include:
- Apple Filing Protocol (AFP)
- Independent Computing Architecture (ICA), the Citrix system core protocol
- Lightweight Presentation Protocol (LPP)
- NetWare Core Protocol (NCP)
- Network Data Representation (NDR)
- Telnet (a remote terminal access protocol)
- Tox, The Tox protocol is sometimes regarded as part of both the presentation and application layer
- eXternal Data Representation (XDR)
- X.25 Packet Assembler/Disassembler Protocol (PAD)
Osi Model Layer 2 Protocols
References[edit]
Which Osi Layer Provides File Transfer Services Online
- ^ abcDean, Tamara (2010). Network+ Guide to Networks. Delmar. pp. 44–47.
- ^ abcdeMicrosoft TechNet
- ^Grigonis, Richard (2000). Computer telephony encyclopedia. CMP. p. 331.
- ^http://www.linfo.org/presentation_layer.html Linux Information Project
- ^ abHura, Gurdeep (2001). 'Application Layer'. Data and Computer Communications: Networking and Internetworking. CRC Press LLC. pp. 710–712.